Zerto Real-Time Encryption Detection
Respond quickly to ransomware encryption attacks, and recover effectively with the lowest amount of data loss and downtime
Moving to Real-Time Ransomware Detection
Periodic ransomware detection methods aren’t fast enough to keep up with the pace of today’s rapidly evolving security landscape. They should be complemented with faster ones that can detect ransomware encryption attacks as soon as possible.
Zerto Real-Time Encryption Detection - Overview
To exit, click outside the video
Connecting Detection to Recovery
Historically, ransomware detection has relied on three major approaches spanning both direct and indirect methods: signature-based, honeypots and anomaly-based detection—also called "signatureless".
The latter is very popular, however, many of the vendors developing these solutions are cybersecurity-centric. So, while these solutions are strong for security and are a key part of any well-rounded security stack, they are decoupled from recovery, an essential phase in mitigating and recovering from ransomware.
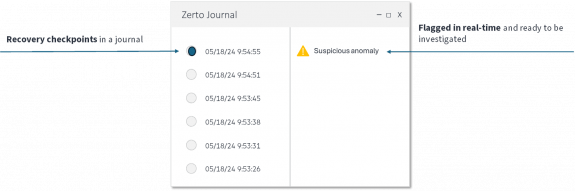
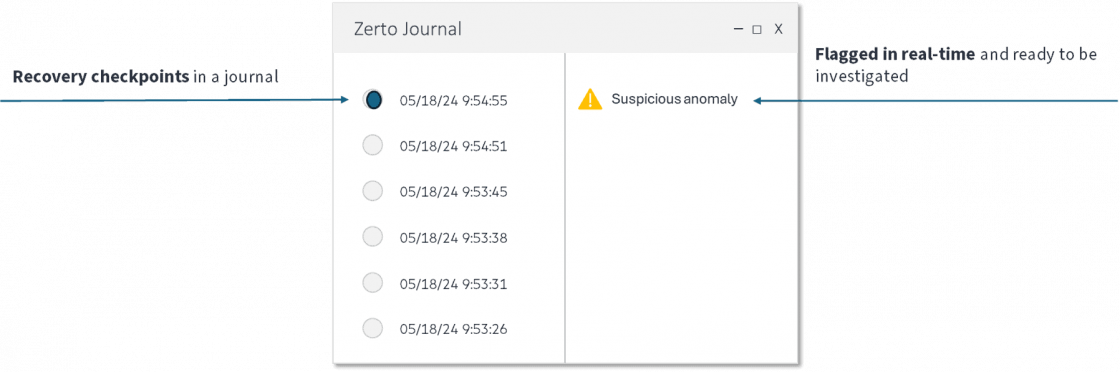
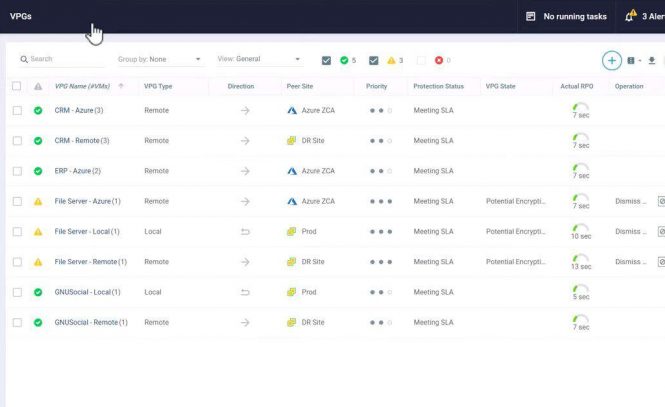
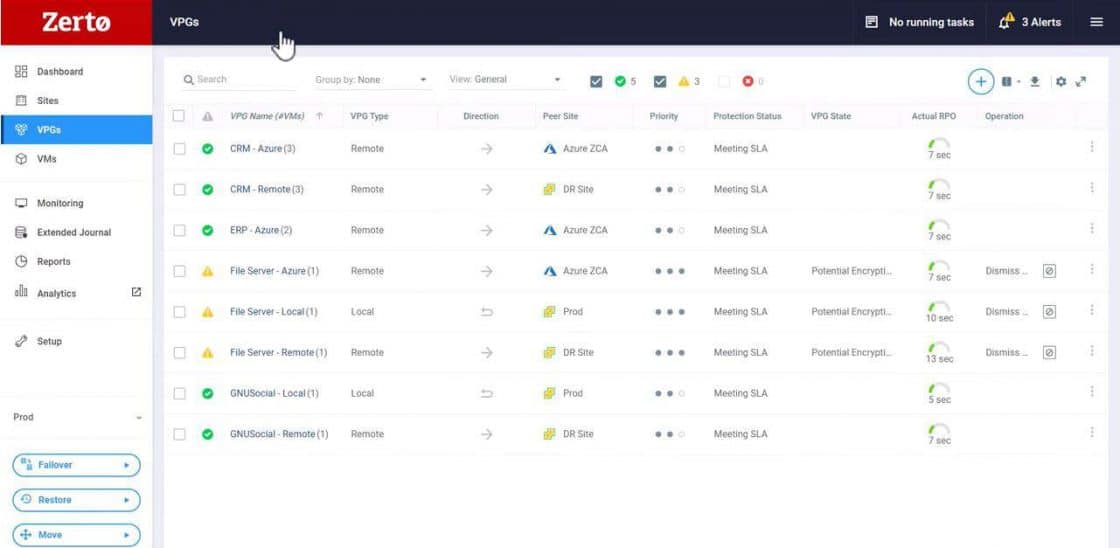
Zerto has real-time encryption detection that fixes that gap as it connects detection with recovery into one solution. It enables security and IT Ops teams to go from response to recovery in a unified and effective fashion by 1) detecting a ransomware encryption attack at its earliest stage, and 2) making it easy to identify the most recent and clean restore point from which to start the recovery process.
Continuous, Real-Time Ransomware Detection
Zerto has an always-on, near-synchronous replication engine—part of the unique continuous data protection in Zerto—which unlocks the ability to analyze data on a virtually real-time basis with high degrees of granularity.
Security teams no longer need to wait until a backup is run—or worse, wait until the backup window ends—to start scanning.
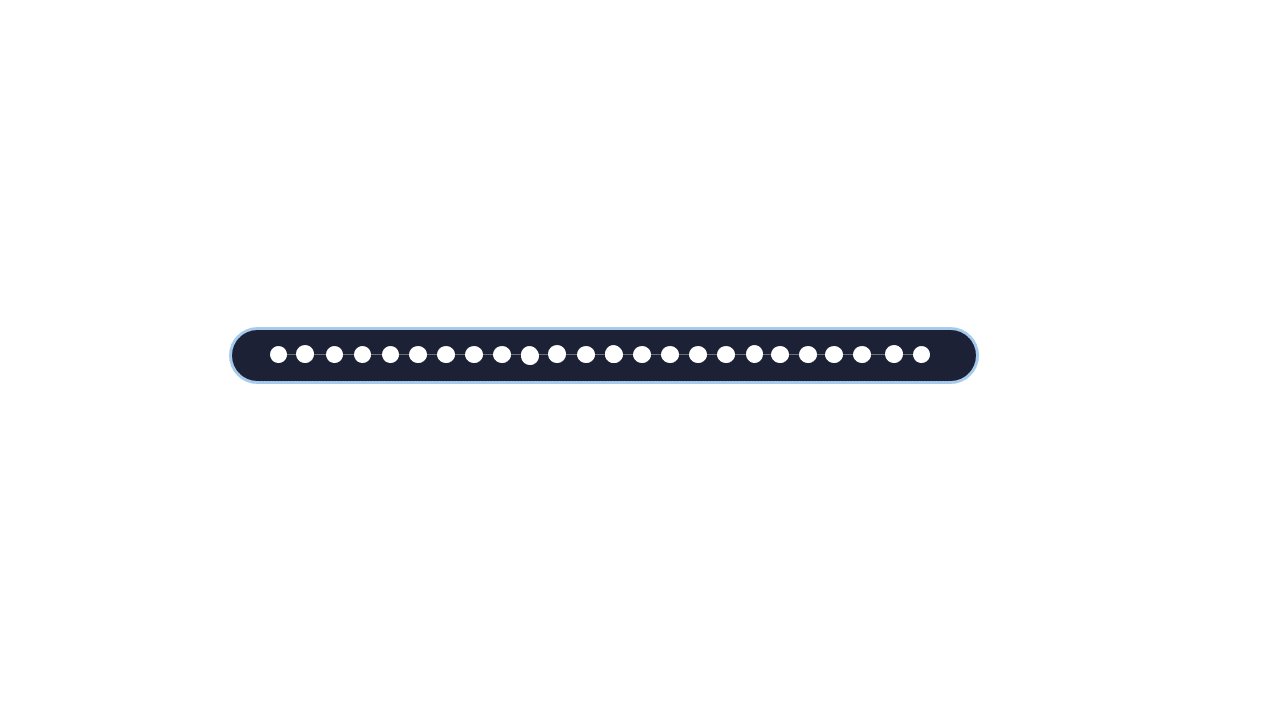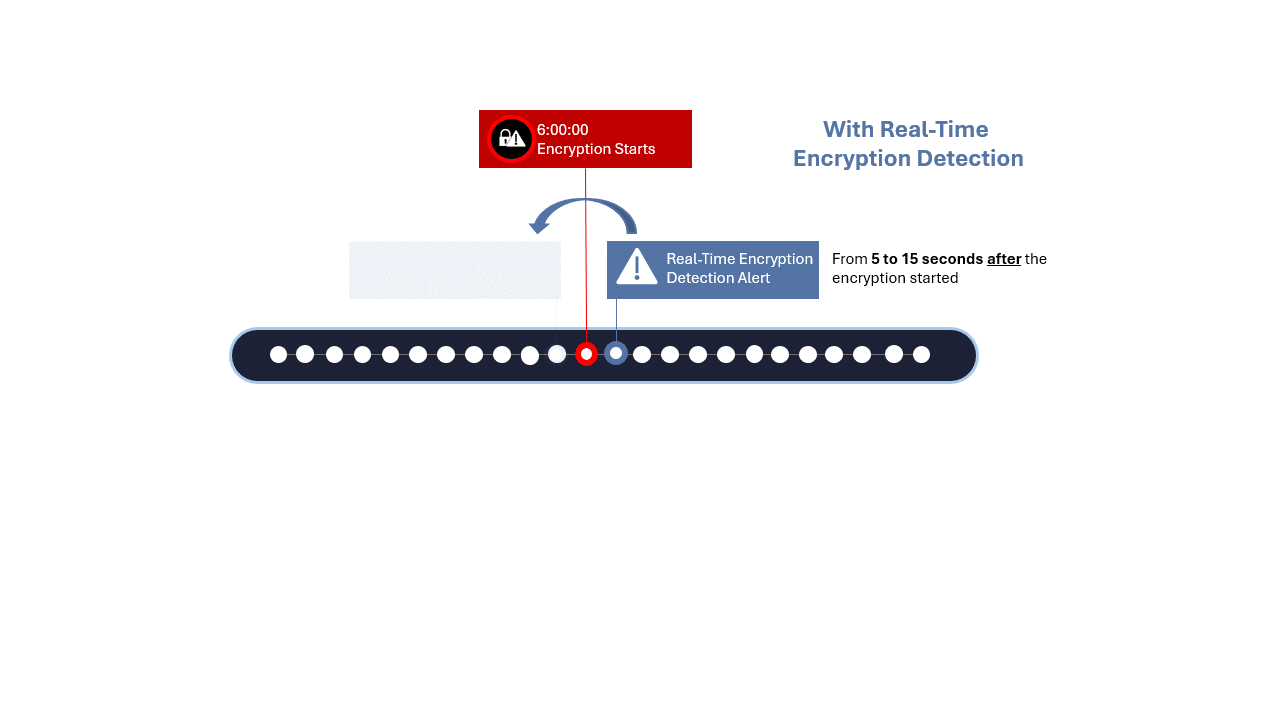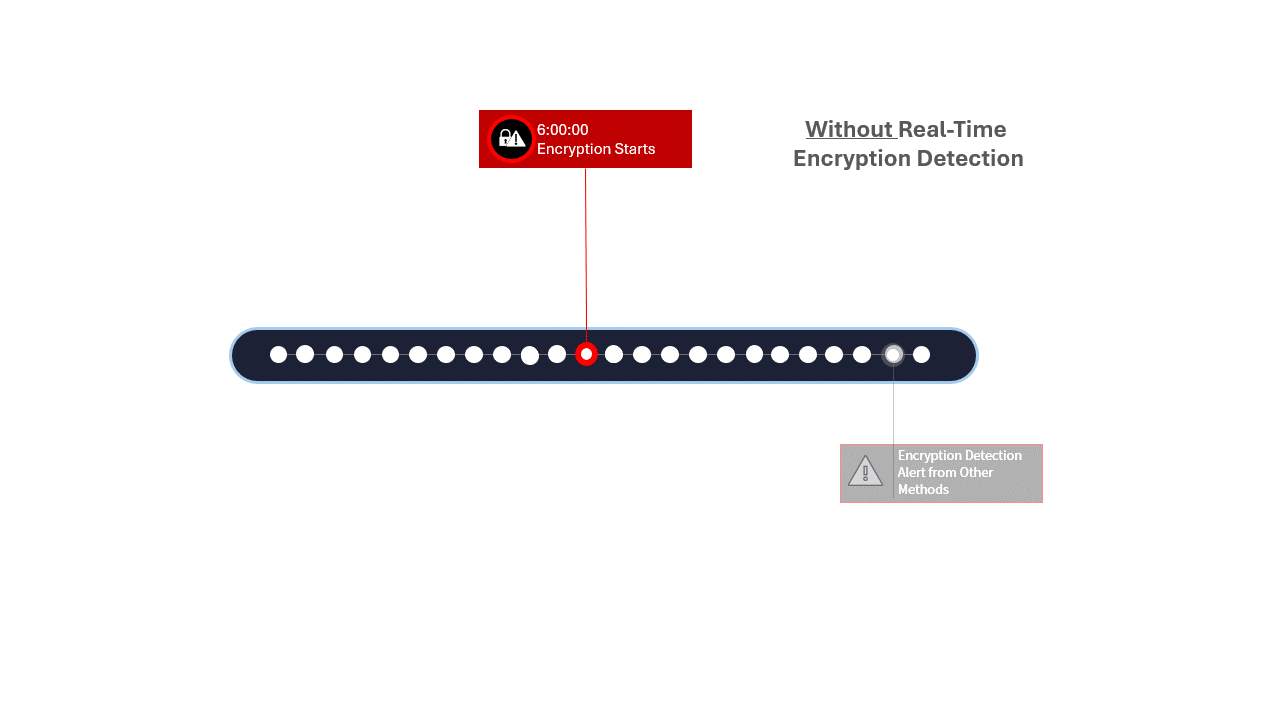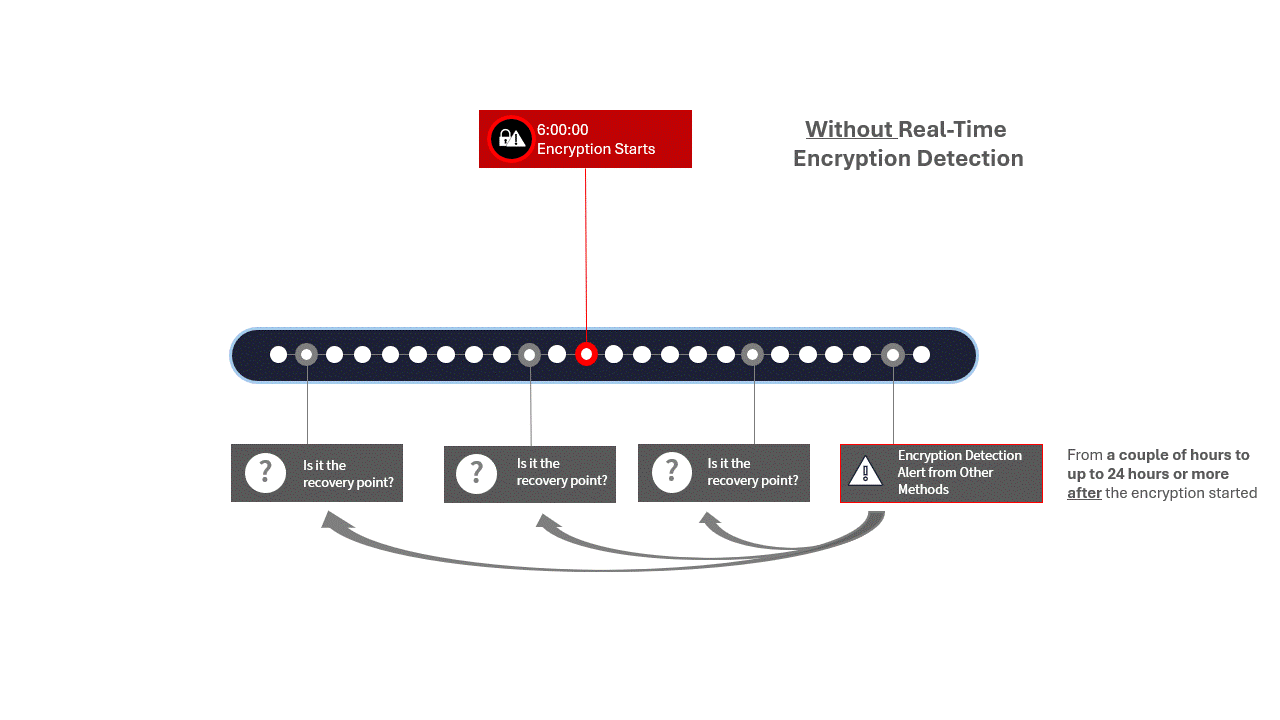
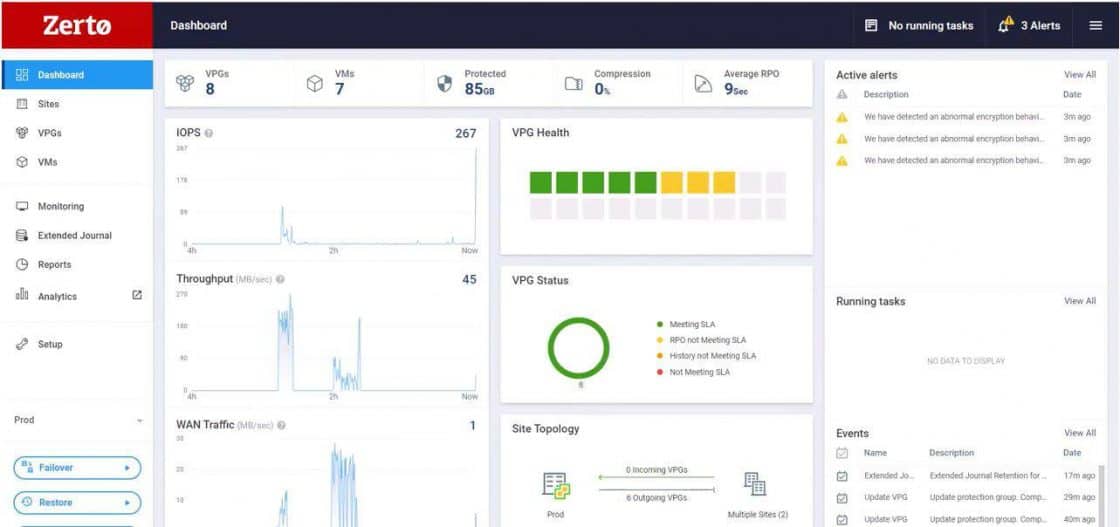
Zerto is a software-only solution that applies algorithmic intelligence to alert you within seconds when there’s an encryption anomaly that could signal the start of a ransomware’s detonation phase.
Zerto Real-Time Ransomware Detection
Zerto Always-On Replication
Rapid Recovery and Reduced Blast Radius
Real-time detection can help your response team to save the amount of data locked by a ransomware attack significantly, limiting its blast radius.
The other benefit of real-time encryption detection, when coupled with a data protection solution, is that it enables your security and IT teams to quickly find and accurately determine the point of impact and therefore to know what data copies to use for your recovery.
Zerto has always-on and real-time detection that can send alerts at the onset of a ransomware detonation phase while providing granular restore points—every 5 to 15 seconds apart— from which to start the recovery process.
This ensures the fastest response possible from detection to recovery, with the minimal amount of data loss and downtime.
Why Real-Time Encryption Detection Matters
Understanding the True Cost of Downtime

Detection at No Additional Cost
Real-time encryption detection is included out of the box with Zerto.
There are no paid add-ons, and no extra subscription to pay for. You simply get more out your data protection solution at no extra cost.
Learn About Ransomware Detection
Benefits of Zerto Real-Time Encryption Detection
Zerto CDP is always-on and functions in real time, essential to recovery. This foundation of block-based (not file-based), hypervisor-level replication also unlocks other benefits for encryption detection:
How Zerto Real-Time Encryption Detection Works
Zerto leverages its proprietary continuous data protection to apply the Zerto Encryption Analyzer on the stream of data being replicated.
Zerto’s encryption analyzer uses a signatureless approach to detect encryption. It assesses data patterns and analyzes entropy to detect unusual encryption that may indicate the locking phase of a ransomware attack has begun.
The Encryption Analyzer works in three main phases: Collection, Inspection, and Reaction (CIR). Together, the CIR
process phases make up the combined real-time encryption detection in Zerto.
Finally, Zerto uses the existing VRAs and ZVMs, that are required for normal CDP operations for analyzing the stream of data without interfering with the replication process.
Understanding Real-Time Encryption Detection with Zerto
APIs for Integration with Your SIEM, SOAR and More
Leverage Zerto open RESTful APIs, based on Swagger, to integrate Zerto Encryption Analyzers with your existing security or observability stack.
Stream the real-time detection and all associated alerts to the EDR (endpoint detection and response), SIEM (security infiormation event management) or SOAR (security orchestration, automation and response) of your choice, including powerful visualizations using open-source software such as Prometheus and Grafana.
And contrary to many vendors, Zerto does not use a closed black box—where customers have no access to detection data. Security and IT teams can customize the solution, integrate it with others, or apply existing workflows (such as in-house AI/ML) to the detection dataset.
Zerto APIs
Zerto Encryption Analyzer: API Endpoints
Key Business Outcomes
Frequently Asked Questions
How does the real-time encryption detection in Zerto work?
Zerto, and its Zerto Encryption Analyzer, is built on a foundation of continuous data protection (CDP), a technology widely considered to be the best way to reduce data loss and downtime.
The proprietary CDP engine in Zerto has been battle-tested and proven at scale, resulting in thousands of customers achieving RPOs of seconds whether protecting 70 or 700 VMs—or even 7,000 VMs simultaneously.
Zerto’s software-only solution applies algorithmic intelligence to alert you within seconds when there’s an encryption anomaly that could signal the start of ransomware’s detonation phase.
What are the benefits of encryption detection through Zerto?
Zerto CDP is essential to recovery, but this foundation of block-based (not file-based), hypervisor-level replication unlocks five primary benefits for encryption detection as well, including:
- Real-time: The always-on, near-synchronous replication engine in Zerto unlocks the ability to analyze data on a virtually real-time basis with high degrees of granularity.
- Agnostic: the type of file being encrypted doesn't matter. Detected encryption is what matters.
- Adaptive: The Zerto Encryption Analyzer is dynamically adaptive. New or different environmental variables do not require any manual update.
- Agentless: Zerto does not use any agents on protected VMs, therefore eliminating the opportunity to get these agents disabled or hijacked.
- Lightweight and non-disruptive: There are no additional components to deploy and configure—Zerto uses the existing Virtual Replication Appliances (VRAs) and Zerto Virtual Managers (ZVMs) that are required for normal CDP and are already lightweight. And the encryption analyses do not interfere with the replication process.
What is the ransomware detection method Zerto uses?
Zerto’s encryption analyzer uses a signatureless approach to detect encryption. It assesses data patterns and analyzes entropy to detect unusual encryption that may indicate the locking phase of a ransomware attack has begun. However, unlike other vendors using this approach—which are usually purpose-built data security or cybersecurity vendors—Zerto’s real-time detection is coupled with recovery.
What's Next?
Have a question about our product or capabilities? Contact us, we are here to help!
Try Zerto
Want to give Zerto a try? Get a free 14-day license or access to our on-demand labs.
RECOMMENDED CONTENT SEE ALL
Gorilla Guide to Real-Time Ransomware Detection and Recovery
In this guide learn about the dangers of ransomware, and how early detection can help mitigate a ransomware attack and allow recovery more quickly.
Detecting and Recovering from Ransomware with Zerto
See how Zerto can help mitigate a ransomware attack using a variety of features, including real-time encryption detection.
Detecting and Recovering from Ransomware with Zerto
To exit, click outside the image
Zerto Continuous Data Protection
Learn about the benefits of protecting your business using Zerto's CDP and real-time encryption detection.